Malicious Solana Browser Extension 'Crypto Copilot' Caught Siphoning User Funds Through Hidden Transaction Instructions
A browser extension marketed as a convenient tool for trading Solana cryptocurrencies has been exposed for secretly diverting user funds through concealed transaction instructions, according to cybersecurity researchers at Socket's Threat Research Team.
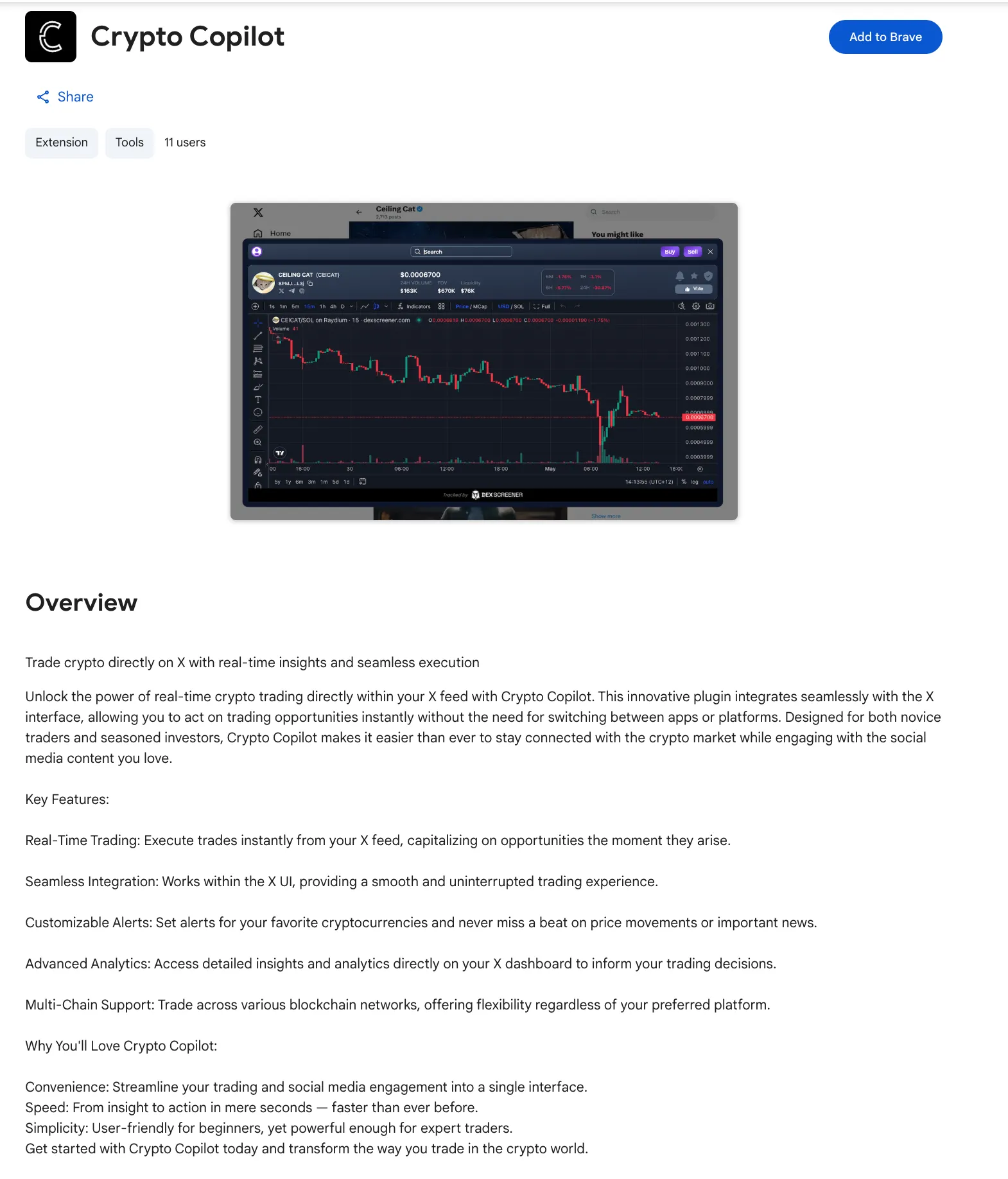
The Chrome extension, named Crypto Copilot, presents itself as a seamless solution for trading SOL tokens directly from the social media platform X (formerly Twitter). However, behind its user-friendly interface lies a sophisticated fraud mechanism that siphons small amounts of cryptocurrency from each transaction executed through the platform.
How the Exploitation Works?
According to Socket's investigation, Crypto Copilot employs a deceptively simple yet effective method to steal funds. When users initiate token swaps through the extension, the software adds a hidden transfer instruction to each transaction that redirects cryptocurrency to an attacker-controlled wallet address.
The malicious code is programmed to divert either 0.05 percent of each transaction's value or a minimum of 0.0013 SOL—whichever amount is greater. This dual-threshold approach ensures attackers receive meaningful returns even from smaller trades while keeping individual losses small enough to evade immediate detection.
The extension leverages Raydium, a legitimate automated market maker operating on the Solana blockchain, to process these swaps. By appending a hidden SystemProgram.transfer instruction to each trade, the software creates what blockchain developers call an "atomic transaction"—multiple operations bundled together that either all succeed or all fail as a single unit.
This technical approach proves particularly insidious because users reviewing their transaction confirmations see only a summary of the primary swap. The confirmation screens display the expected token exchange without revealing the additional transfer instruction embedded within the same atomic transaction. By the time users approve what appears to be a straightforward trade, they've unknowingly authorized the hidden fund diversion as well.
Concealment Through Obfuscation
Socket's researchers documented multiple techniques Crypto Copilot employs to hide its malicious functionality from both users and security reviewers. The extension's code undergoes minification—a process that removes unnecessary characters and compresses the source code, making it significantly more difficult for security analysts to read and audit.
Beyond minification, the developers implemented variable renaming throughout the codebase, replacing descriptive names with meaningless character combinations. This obfuscation layer further complicates efforts to identify suspicious code patterns during security reviews.
The extension maintains ongoing communication with a backend server hosted at crypto-coplilot-dashboard.vercel.app, where it performs several tracking functions. According to Socket's findings, this server registers connected wallet addresses, monitors user activity patterns, and logs referral data—creating a comprehensive surveillance infrastructure alongside the fund diversion mechanism.
Investigators also identified a second domain associated with the operation: cryptocopilot.app. However, this domain currently remains parked without any functional content. Socket researchers noted this absence as a red flag, since legitimate cryptocurrency trading platforms typically maintain active dashboards where users can monitor their activity, review transaction history, and access support resources.
Timeline and Distribution
Crypto Copilot appeared on the Chrome Web Store in mid-2024, positioning itself within the growing ecosystem of browser-based cryptocurrency trading tools. The extension marketed its primary feature as enabling instant Solana trading directly from social media platforms—a convenience factor designed to attract users seeking streamlined trading experiences.
While Socket's report indicates that installation numbers have remained relatively low, the cybersecurity firm emphasized that even limited adoption creates significant risks. For frequent traders executing multiple swaps daily or weekly, the incremental fund diversions can accumulate to substantial amounts over time. The small percentage taken from each transaction means users may not immediately notice the losses, allowing the fraud to continue undetected across dozens or hundreds of trades.
The low-profile nature of these incremental thefts represents a calculated strategy. Unlike dramatic wallet drains that immediately alert victims and trigger security responses, gradual siphoning exploits psychological and practical barriers to detection. Users often attribute minor discrepancies to network fees, slippage, or miscalculations rather than investigating potential fraud.
Broader Context of Browser Extension Threats
The Crypto Copilot incident fits within a troubling pattern of malicious browser extensions targeting cryptocurrency users. Industry reports have documented numerous previous cases involving compromised Chrome and Firefox extensions designed to exploit popular wallet applications, including MetaMask, Phantom, and Coinbase.
These attacks typically follow similar patterns: developers create extensions offering legitimate-seeming functionality—portfolio tracking, trading automation, price alerts, or social media integration—while embedding malicious code that compromises user security. The browser extension model provides attackers with powerful capabilities, including the ability to inject code into web pages, intercept form submissions, and monitor user interactions across websites.
Browser extensions operate with elevated privileges that make them particularly dangerous when compromised. Once installed, these tools can read and modify content on websites users visit, access clipboard data, and in some cases intercept or modify network requests. For cryptocurrency applications, these capabilities create numerous attack vectors.
The challenge for both users and platform operators stems from the difficulty of distinguishing legitimate extensions from malicious ones at the point of installation. Many fraudulent extensions feature professional-looking descriptions, fabricated user reviews, and interfaces that closely mimic trusted applications. By the time security researchers identify and report malicious extensions, significant damage may already have occurred.
Technical Implications for DeFi Security
The Crypto Copilot case illuminates fundamental vulnerabilities in how browser-based tools interact with blockchain networks. Solana's transaction model, like those of other blockchains, allows multiple instructions to be bundled within a single atomic transaction. While this capability serves legitimate purposes—enabling complex DeFi operations that require multiple steps to complete successfully—it also creates opportunities for malicious actors to hide unauthorized operations within seemingly routine transactions.
Standard wallet interfaces typically display transaction summaries rather than complete instruction-by-instruction breakdowns. This design choice prioritizes user experience and readability over exhaustive technical disclosure. For most legitimate transactions, summary views provide sufficient information for users to verify they're authorizing the intended operation.
However, this same interface design becomes a vulnerability when malicious software exploits the gap between what users see and what transactions actually contain. The atomic nature of bundled transactions means users cannot selectively approve or reject individual instructions—they must either approve the entire bundle or reject it entirely.
Socket's researchers emphasized this represents a significant security challenge for decentralized finance ecosystems. As DeFi platforms and tools become more sophisticated, transaction complexity increases, creating additional opportunities for malicious actors to embed hidden instructions that escape user notice.
Risk Assessment and Impact
While Crypto Copilot's installation base remains limited according to available data, Socket warned against dismissing the threat based on current adoption levels. The cybersecurity firm's analysis highlighted several factors that amplify the risk beyond simple user count calculations.
Active traders who frequently execute swaps face disproportionate exposure. Someone conducting ten trades daily would lose 0.5 percent of their total trading volume to the hidden diversions, amounts that compound significantly over weeks or months. For professional or high-volume traders, these cumulative losses could reach thousands of dollars before detection.
The extension's design also enables the attackers to scale their operation efficiently. Unlike phishing schemes that require continuous social engineering efforts or one-time wallet drains that quickly alert victims and security teams, the incremental siphoning model generates passive income that grows proportionally with user adoption and trading activity.
Additionally, the tracking infrastructure Socket identified suggests the operators maintain detailed surveillance of victim behavior. The backend server's collection of wallet addresses, activity patterns, and referral data could support more sophisticated follow-on attacks or enable the sale of user data to other malicious actors.
Detection and Prevention Challenges
Several factors make Crypto Copilot-style attacks particularly difficult to detect and prevent. The Chrome Web Store review process, while designed to filter out malicious software, faces inherent limitations when evaluating code that employs sophisticated obfuscation techniques.
Browser extension stores process thousands of submissions and updates, creating practical constraints on the depth of security review each submission receives. Automated scanning tools can identify known malware signatures and certain suspicious patterns, but novel attack methods or well-obfuscated code may pass initial screenings.
Furthermore, extensions can be updated after initial approval. While major platforms conduct reviews of updates, the time lag between malicious update deployment and security response creates windows of vulnerability. Attackers sometimes publish legitimate extensions, build user bases and positive reviews, then introduce malicious functionality through updates—a tactic known as a "time bomb" attack.
For individual users, verifying extension safety presents significant challenges. Most people lack the technical expertise to audit source code, even if unobfuscated versions were readily available. Traditional trust signals—installation counts, positive reviews, professional presentation—can be manipulated or, in the case of newer extensions, simply absent without indicating malicious intent.
Recommended Security Practices
In response to the Crypto Copilot exposure, Socket and other security researchers have outlined several protective measures for cryptocurrency users who utilize browser-based trading tools.
Transaction verification stands as the primary defense. Users should carefully review all transaction details before approval, understanding that confirmation screens may not display complete information about bundled instructions. When possible, traders should use wallet interfaces that provide detailed instruction-level breakdowns of atomic transactions rather than relying solely on summary views.
Extension legitimacy verification requires multilayered evaluation. Users should research extensions before installation, looking beyond store listings to independent security reviews, developer credentials, and community discussions. Established extensions with long operating histories and verified publishers present lower risk profiles than recently published tools from unknown developers.
Monitoring wallet activity for unexpected outflows helps identify compromises after they occur. While the small percentage diversions in the Crypto Copilot case might escape casual notice, a systematic review of transaction records can reveal patterns of unauthorized transfers. Users should reconcile their expected token balances with actual holdings regularly, investigating any discrepancies.
Cybersecurity researchers recommend staying informed about emerging threats through trusted security firms and blockchain security communities. Organizations like Socket, PeckShield, and CertiK regularly publish threat intelligence that alerts users to newly identified malicious tools and attack patterns.
Platform and Ecosystem Responses
The Crypto Copilot incident raises questions about the responsibilities and capabilities of platform operators in preventing such attacks. Browser extension stores face competing priorities: maintaining accessibility for legitimate developers while implementing security measures that effectively filter malicious software without creating prohibitive barriers to entry.
Enhanced monitoring systems could improve threat detection. Automated analysis that specifically examines how extensions interact with blockchain transactions might flag suspicious patterns like hidden transfer instructions or unusual network communications. Machine learning models trained on known malicious extension behaviors could supplement traditional signature-based detection.
However, technical solutions alone may prove insufficient. The fundamental challenge stems from the trusted position browser extensions occupy. Once installed with user permission, these tools operate with capabilities necessary for legitimate functionality but exploitable for malicious purposes.
Some security experts advocate for more restrictive permission models where extensions must explicitly declare and justify specific capabilities before installation. Users would receive clearer warnings about what access they're granting, potentially reducing blind trust in extension requests. However, such models risk creating "permission fatigue" where users automatically approve requests without reading them—a behavior that limits effectiveness.
Implications for DeFi Adoption
Security incidents like the Crypto Copilot exposure create broader implications for cryptocurrency and decentralized finance adoption. As blockchain technology seeks mainstream acceptance, user protection becomes increasingly critical. High-profile frauds and security failures undermine confidence and may deter potential users who perceive the ecosystem as unsafe.
The browser-based trading tools at the center of this incident represent efforts to improve cryptocurrency accessibility and user experience. By integrating trading functionality directly into familiar platforms like social media sites, developers aim to reduce friction and make blockchain technology more approachable for non-technical users.
However, this convenience-security tradeoff requires careful navigation. The same browser integrations that simplify user experience also create new attack surfaces and expand the trust assumptions users must make. Moving custody and transaction authorization through additional software layers introduces points of potential compromise.
The decentralized nature of blockchain networks, often cited as a security advantage, provides limited protection against attacks that occur at the application layer. While on-chain transactions remain cryptographically secure and transparent, users who authorize those transactions through compromised interfaces lose the benefits of blockchain's trustless architecture.
Looking Forward
As browser-based cryptocurrency tools continue proliferating, the security challenges they present will likely intensify. The financial incentives for attackers remain substantial, while the technical sophistication required to create convincing malicious extensions continues decreasing as development tools and frameworks become more accessible.
Socket's report concluded with emphasis on the need for enhanced monitoring and oversight within browser extension ecosystems. The cybersecurity firm suggested that protecting decentralized finance users will require coordinated efforts across multiple stakeholders: platform operators implementing stronger review processes, security researchers conducting ongoing threat surveillance, wallet developers building more transparent transaction interfaces, and users adopting defensive practices.
The Crypto Copilot case serves as a reminder that security in cryptocurrency ecosystems extends far beyond blockchain protocols themselves. As the technology stack supporting blockchain interactions grows more complex—incorporating browser extensions, mobile applications, hardware devices, and cloud services—each component introduces potential vulnerabilities that require attention and protection.
For the Solana ecosystem specifically, this incident highlights the importance of transaction transparency and user education. While Solana's technical architecture supports the high-speed, low-cost transactions that make it attractive for DeFi applications, those same capabilities can be exploited when users lack clear visibility into what their transaction approvals authorize.
The continuing evolution of cryptocurrency security will require balancing innovation with protection, accessibility with vigilance, and user convenience with informed consent. As the Crypto Copilot exposure demonstrates, that balance remains a work in progress with real consequences for users who find themselves on the wrong side of the equation.

![The backend domain used by the extension crypto-coplilot-dashboard[.]vercel.app loads only a blank placeholder page, despite the extension sending wallet identifiers to its API. The main domain cryptocopilot[.]app is parked and not associated with any real product, reinforcing that the extension has no legitimate supporting infrastructure. The backend domain used by the extension crypto-coplilot-dashboard[.]vercel.app loads only a blank placeholder page, despite the extension sending wallet identifiers to its API. The main domain cryptocopilot[.]app is parked and not associated with any real product, reinforcing that the extension has no legitimate supporting infrastructure.](https://cdn.sanity.io/images/cgdhsj6q/production/e7a75ebe07ebc88e52afd11fffabd0b46d25d725-2048x625.png?w=1600&q=95&fit=max&auto=format)




No comments